44 security labels access control
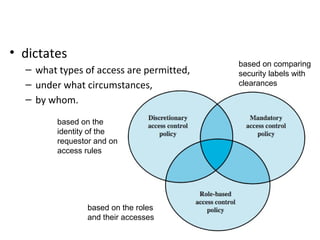
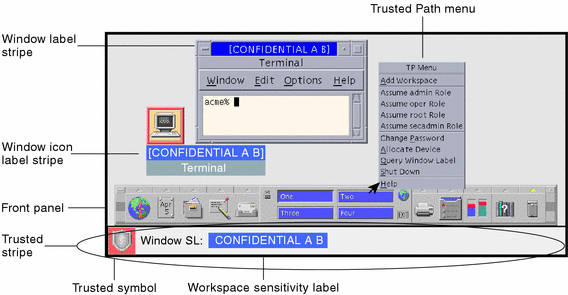
cloud.google.com › column-level-security-introIntroduction to column-level access control | BigQuery ... 2 days ago · Using BigQuery column-level access control, you can create policies that check, at query time, whether a user has proper access. For example, a policy can enforce access checks such as: You must be in group:high-access to see the columns containing TYPE_SSN. To enhance column-level access control, you can optionally use dynamic data masking ... en.wikipedia.org › wiki › Mandatory_access_controlMandatory access control - Wikipedia Sun's Trusted Solaris uses a mandatory and system-enforced access control mechanism (MAC), where clearances and labels are used to enforce a security policy. However note that the capability to manage labels does not imply the kernel strength to operate in multilevel security mode [ citation needed ] .
abcnews.go.com › internationalInternational News | Latest World News, Videos & Photos -ABC ... Oct 18, 2022 · Get the latest international news and world events from Asia, Europe, the Middle East, and more. See world news photos and videos at ABCNews.com
Security labels access control
› ictU.S. Access Board - Revised 508 Standards and 255 Guidelines The U.S. Access Board is a federal agency that promotes equality for people with disabilities through leadership in accessible design and the development of accessibility guidelines and standards for the built environment, transportation, communication, medical diagnostic equipment, and information technology. learn.microsoft.com › en-us › microsoft-365Search the audit log in the Microsoft Purview compliance ... Oct 03, 2022 · For more information about the operations that are audited in each of the services listed in the previous table, see the Audited activities section in this article.. The previous table also identifies the record type value to use to search the audit log for activities in the corresponding service using the Search-UnifiedAuditLog cmdlet in Exchange Online PowerShell or by using a PowerShell script. learn.microsoft.com › en-us › securityAzure security baseline for Azure Kubernetes Service ... Jul 07, 2022 · Identity and Access Control. For more information, see the Azure Security Benchmark: Identity and Access Control. 3.1: Maintain an inventory of administrative accounts. Guidance: Azure Kubernetes Service (AKS) itself does not provide an identity management solution which stores regular user accounts and passwords. With Azure Active Directory ...
Security labels access control. learn.microsoft.com › en-us › azureAzure resource provider operations | Microsoft Learn This section lists the operations for Azure resource providers, which are used in built-in roles. You can use these operations in your own Azure custom roles to provide granular access control to resources in Azure. The resource provider operations are always evolving. learn.microsoft.com › en-us › securityAzure security baseline for Azure Kubernetes Service ... Jul 07, 2022 · Identity and Access Control. For more information, see the Azure Security Benchmark: Identity and Access Control. 3.1: Maintain an inventory of administrative accounts. Guidance: Azure Kubernetes Service (AKS) itself does not provide an identity management solution which stores regular user accounts and passwords. With Azure Active Directory ... learn.microsoft.com › en-us › microsoft-365Search the audit log in the Microsoft Purview compliance ... Oct 03, 2022 · For more information about the operations that are audited in each of the services listed in the previous table, see the Audited activities section in this article.. The previous table also identifies the record type value to use to search the audit log for activities in the corresponding service using the Search-UnifiedAuditLog cmdlet in Exchange Online PowerShell or by using a PowerShell script. › ictU.S. Access Board - Revised 508 Standards and 255 Guidelines The U.S. Access Board is a federal agency that promotes equality for people with disabilities through leadership in accessible design and the development of accessibility guidelines and standards for the built environment, transportation, communication, medical diagnostic equipment, and information technology.

















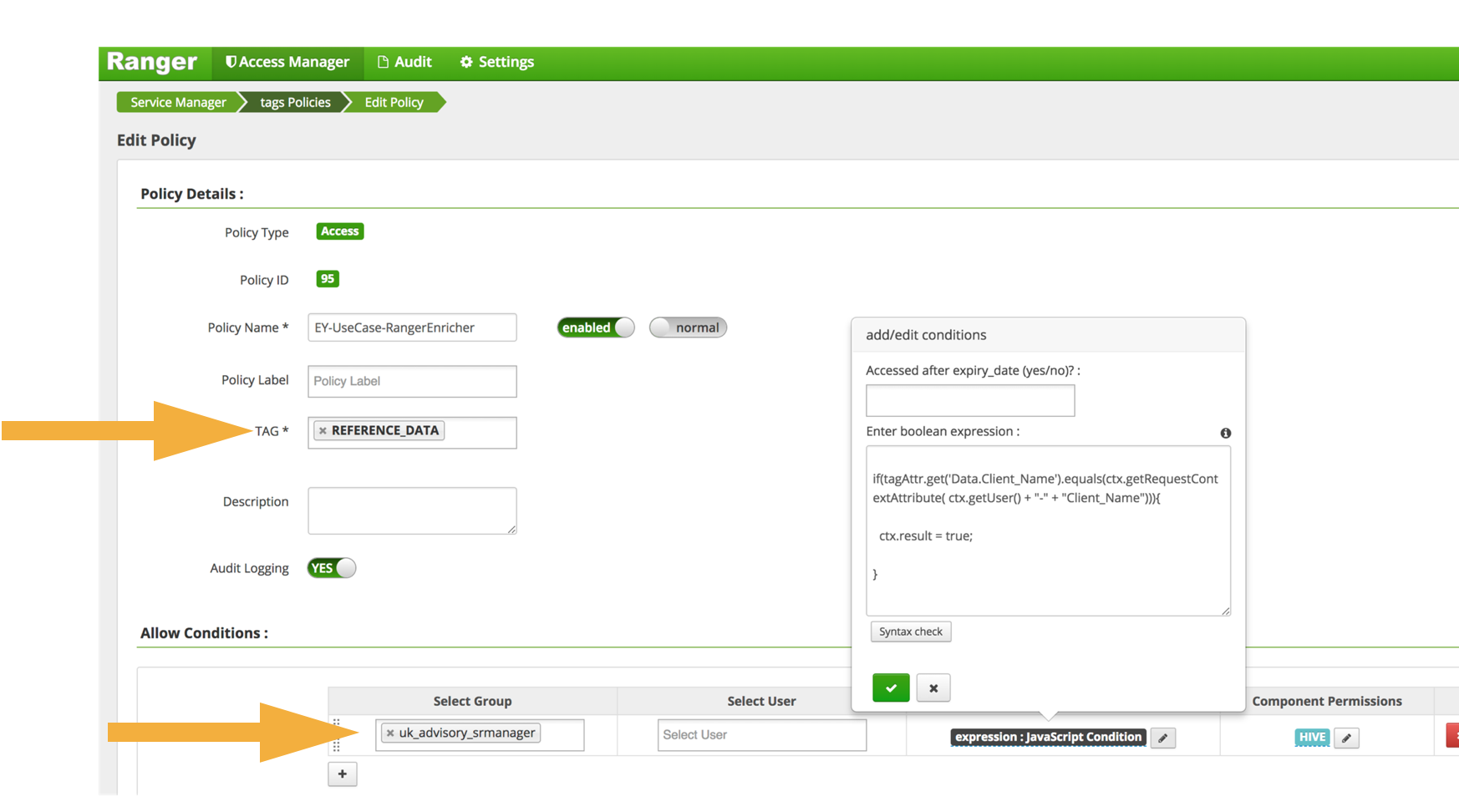



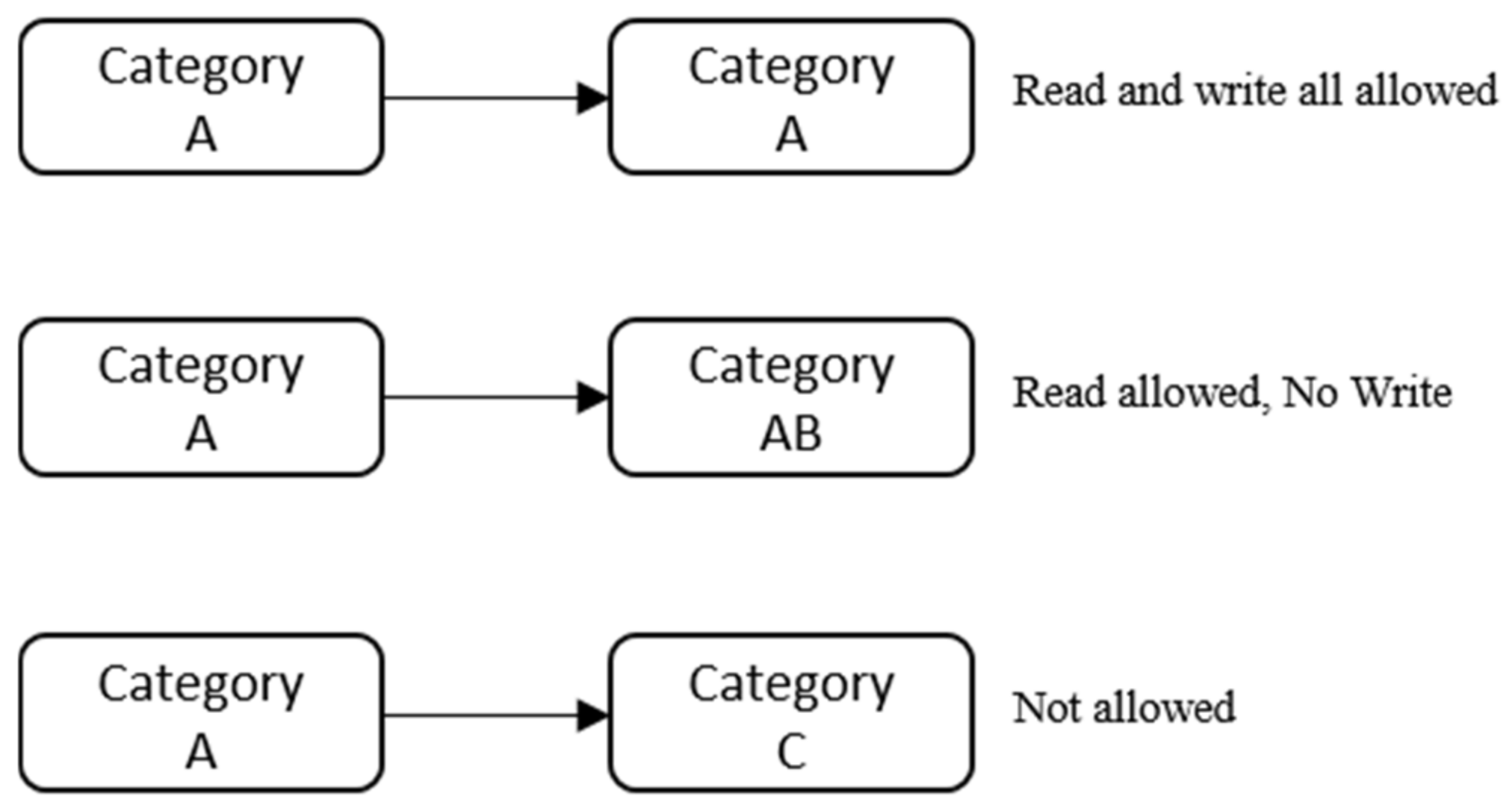
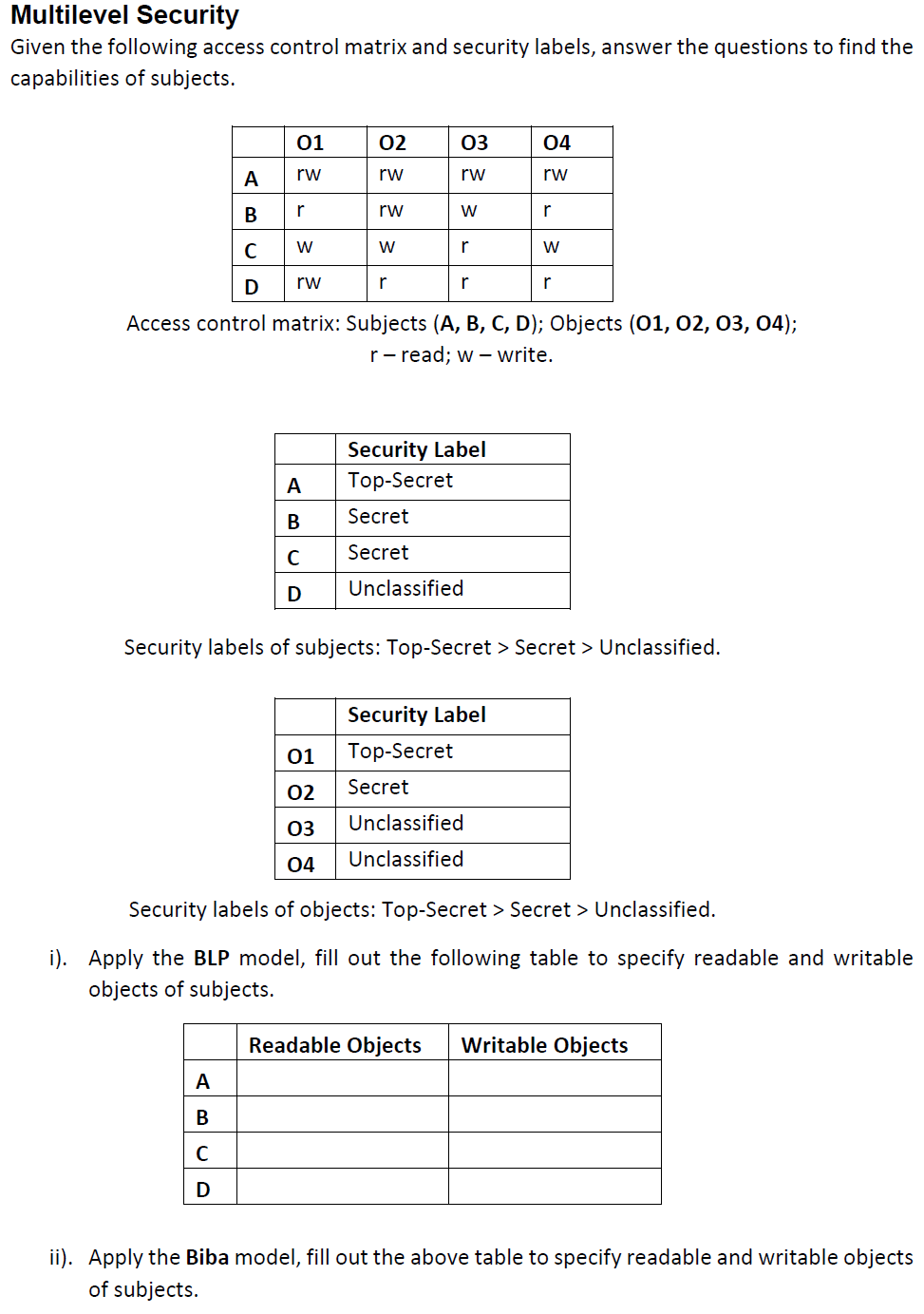
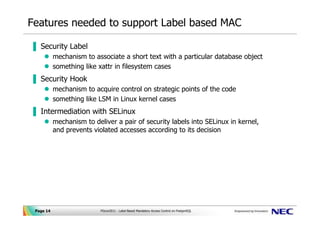




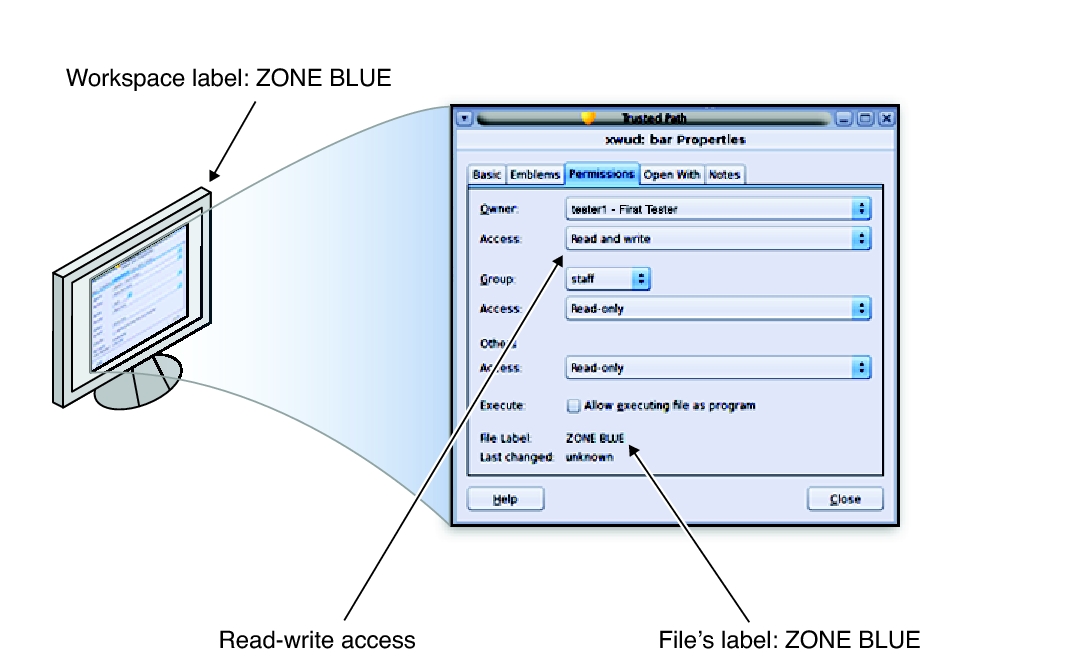


Post a Comment for "44 security labels access control"